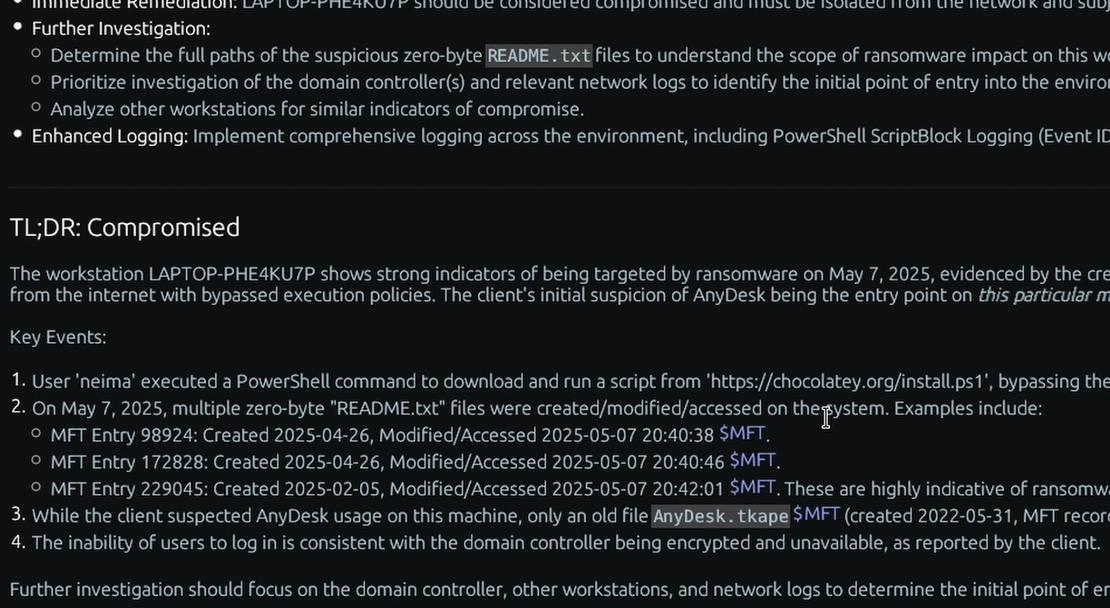
What is the “SRUM” Windows forensic artifact?
The System Resource Usage Monitor (SRUM) is a feature in modern Windows operating systems that collects and stores detailed data about system resource consumption on a per-application basis. Its purpose is to provide insight into how applications are using system resources like the CPU, network, and memory over time. This data is stored in a database file located at %SystemRoot%\System32\sru\SRUDB.dat. SRUM logs information over a rolling 60-day period, capturing a rich historical record of system activity.
For a DFIR investigation, the SRUM database is an exceptionally valuable artifact. The entries provide a wealth of context that is often difficult to find elsewhere. SRUM tracks which user account ran a specific application, the total number of bytes it sent and received over both Wi-Fi and wired networks, and the duration of its execution. This allows an investigator to directly attribute network traffic to a specific process, which is critical for identifying malware C2 communications or data exfiltration. For example, if a seemingly benign process like svchost.exe shows an unusual amount of network outbound traffic, SRUM can help confirm a compromise. It also provides a detailed timeline of application usage, helping to pinpoint when a malicious program was active on the system.
Collecting, Decoding, and Viewing “SRUM” with TensorGuard
- Create a TensorGuard account and sign in to the TensorGuard console at https://app.tensorguard.com.
- Select “Case Manager”, then the plus button to create a case. This will contain your enrolled devices, their reports, and any manually submitted collections.
- Linked inside the case menu, download the TensorGuard Forensic Collector and run it on your target system.
- In the console, click the plus button for “New Enrollment”, copy the enrollment key, and paste it into the TensorGuard Forensic Collector on your target device.
- Now that you have a device enrolled, select the device(s), and click “Send Signal”. Answer the questions regarding what you want to look for in the analysis, any alerting on positive findings, and if the collection and analysis should be recurring.
- Once the report is generated, you’ll have SRUM delivered in the browser, alongside an executive summary and timeline of findings.
Get Started

SRUM
Windows
Details which applications used network data and CPU time, helping to track internet and program activity.
About SRUMStart with a Compromise Assessment.
The best way to see the power of TensorGuard is to use it. For a simple, flat fee, we will conduct a full, AI-powered Compromise Assessment on a selection of your critical systems.