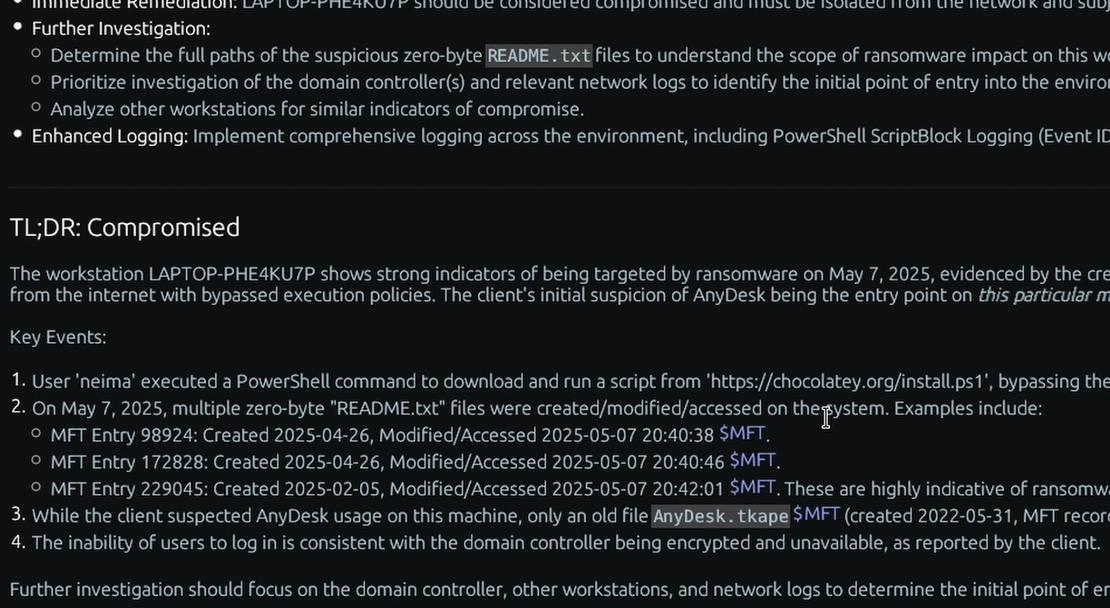
What is the “Slack” forensic artifact?
Slack artifacts consist of the data created and stored by the popular team collaboration application. This information is generated to manage user sessions, cache conversations and files for performance, and maintain workspace configurations. This data is maintained within the user’s profile in a series of application-specific databases and directories, including remote sources, which house details about logged-in accounts, joined workspaces, communication channels, direct messages, and downloaded attachments.
For a DFIR investigator, Slack data provides a direct window into a user’s communications and is a critical resource for internal investigations, particularly those concerning insider risk and insider threats. Analysis of these artifacts can identify all accounts and workspaces accessed from the machine and reconstruct user conversations. This is invaluable for uncovering evidence of data exfiltration, intellectual property theft, or policy violations. Furthermore, in sensitive cases involving potential workplace violence or harassment, the content of messages and shared attachments can provide definitive evidence. By examining these communications and their associated receipts, an investigator can build a comprehensive timeline of a user’s actions, attribute behavior, and understand the context behind an internal incident.
Collecting, Decoding, and Viewing “Slack” with TensorGuard
- Create a TensorGuard account and sign in to the TensorGuard console at https://app.tensorguard.com.
- Select “Case Manager”, then the plus button to create a case. This will contain your enrolled devices, their reports, and any manually submitted collections.
- Linked inside the case menu, download the TensorGuard Forensic Collector and run it on your target system.
- In the console, click the plus button for “New Enrollment”, copy the enrollment key, and paste it into the TensorGuard Forensic Collector on your target device.
- Now that you have a device enrolled, select the device(s), and click “Send Signal”. Answer the questions regarding what you want to look for in the analysis, any alerting on positive findings, and if the collection and analysis should be recurring.
- Once the report is generated, you’ll have Slack delivered in the browser, alongside an executive summary and timeline of findings.
Get Started

Slack
All
A record of user messages and file transfers that provides evidence of conversations and insider threats.
About SlackStart with a Compromise Assessment.
The best way to see the power of TensorGuard is to use it. For a simple, flat fee, we will conduct a full, AI-powered Compromise Assessment on a selection of your critical systems.