Regain internal control over digital forensics and incident response.
Forensic insight, on demand, as a service.
- Evidence-Based Certainty
- Fleet-Wide Scale
Forensic collection as a service.
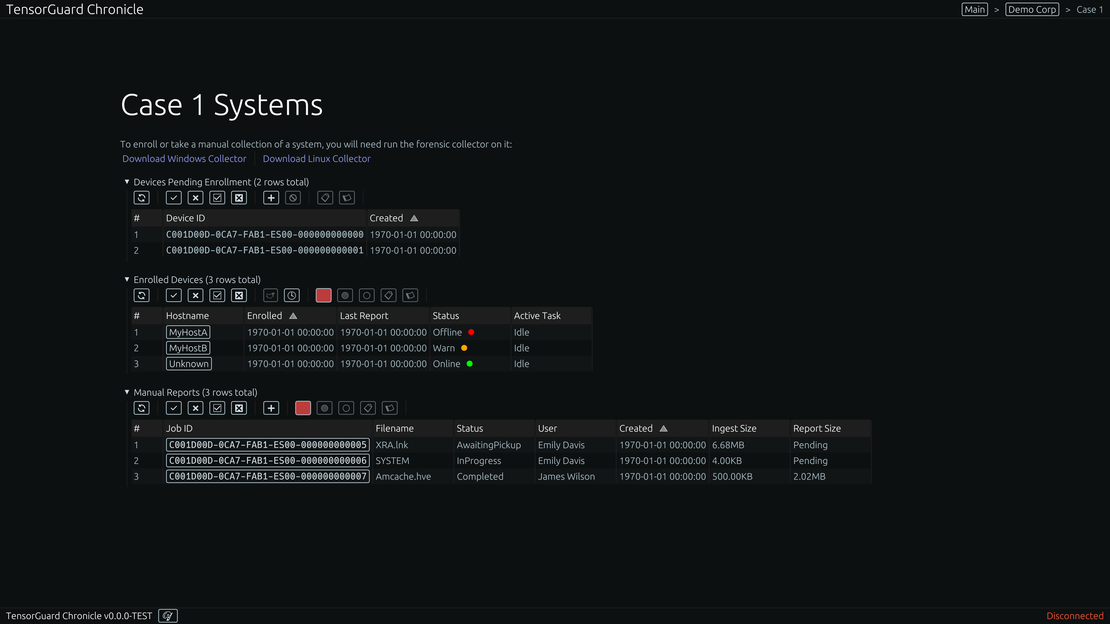
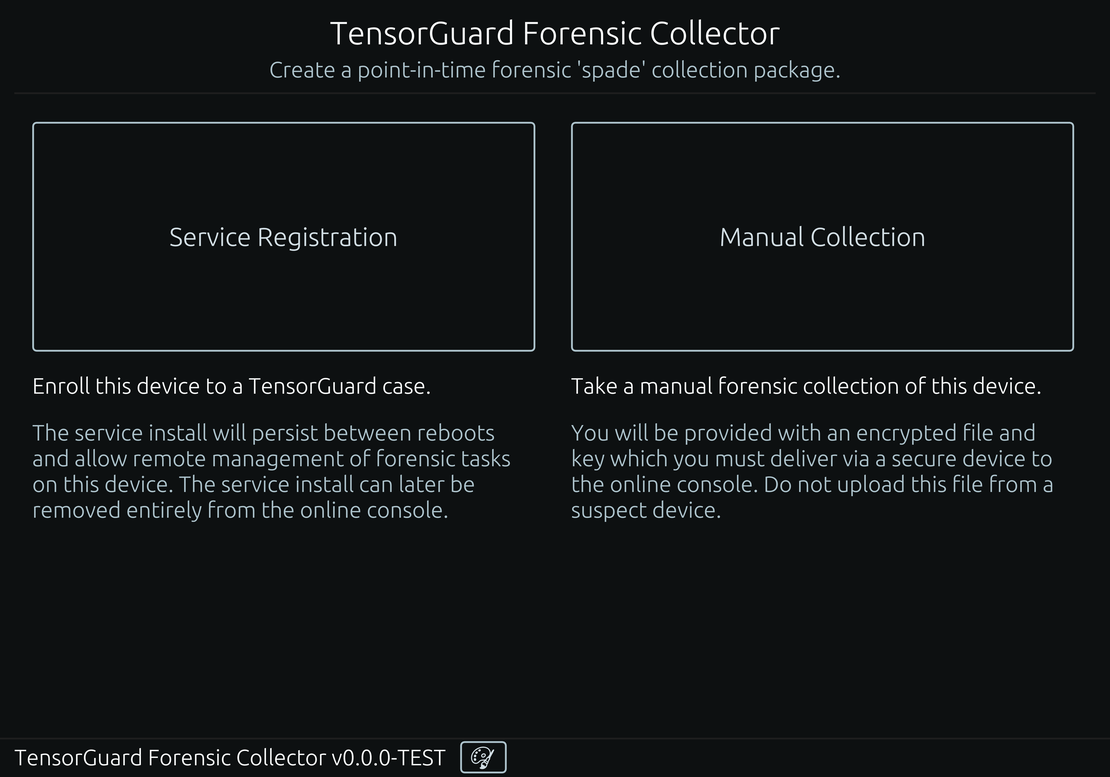
Move beyond the limits of manual investigations. Deploy our lightweight agent to schedule and automate forensic collections across your entire fleet, from servers to endpoints, ensuring you always have a baseline of evidence.
- Unlimited Scale
- Secure Archival
- Automated Collection
- Online/Offline
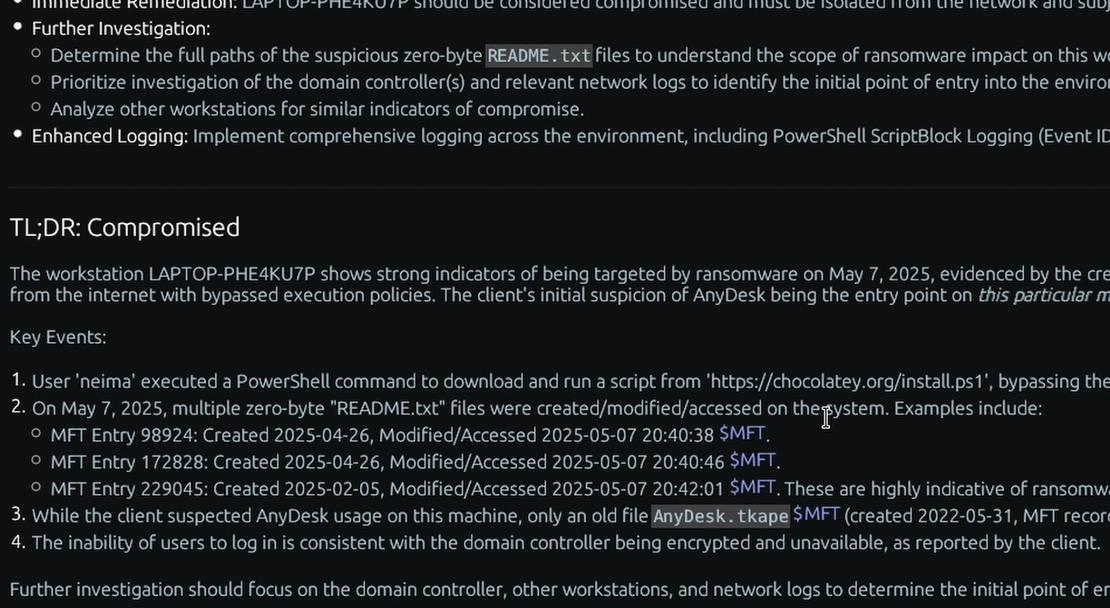
Analysis powered by artificial intelligence.
Our contextual analysis engine—powered by modern AI and proven statistical methods—sifts through gigabytes of artifacts in minutes. We don't give you a data dump; we give you answers.
- Executive Summary
- Remediation Steps
- IoC Timeline
- Raw Evidence
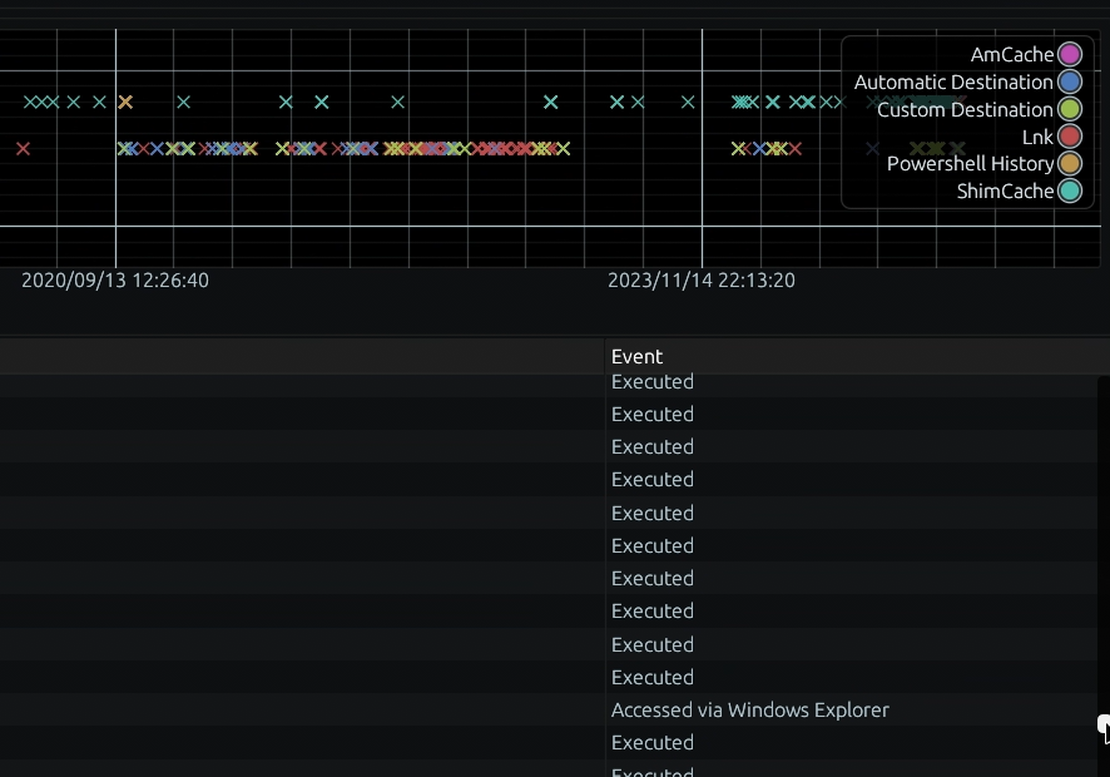
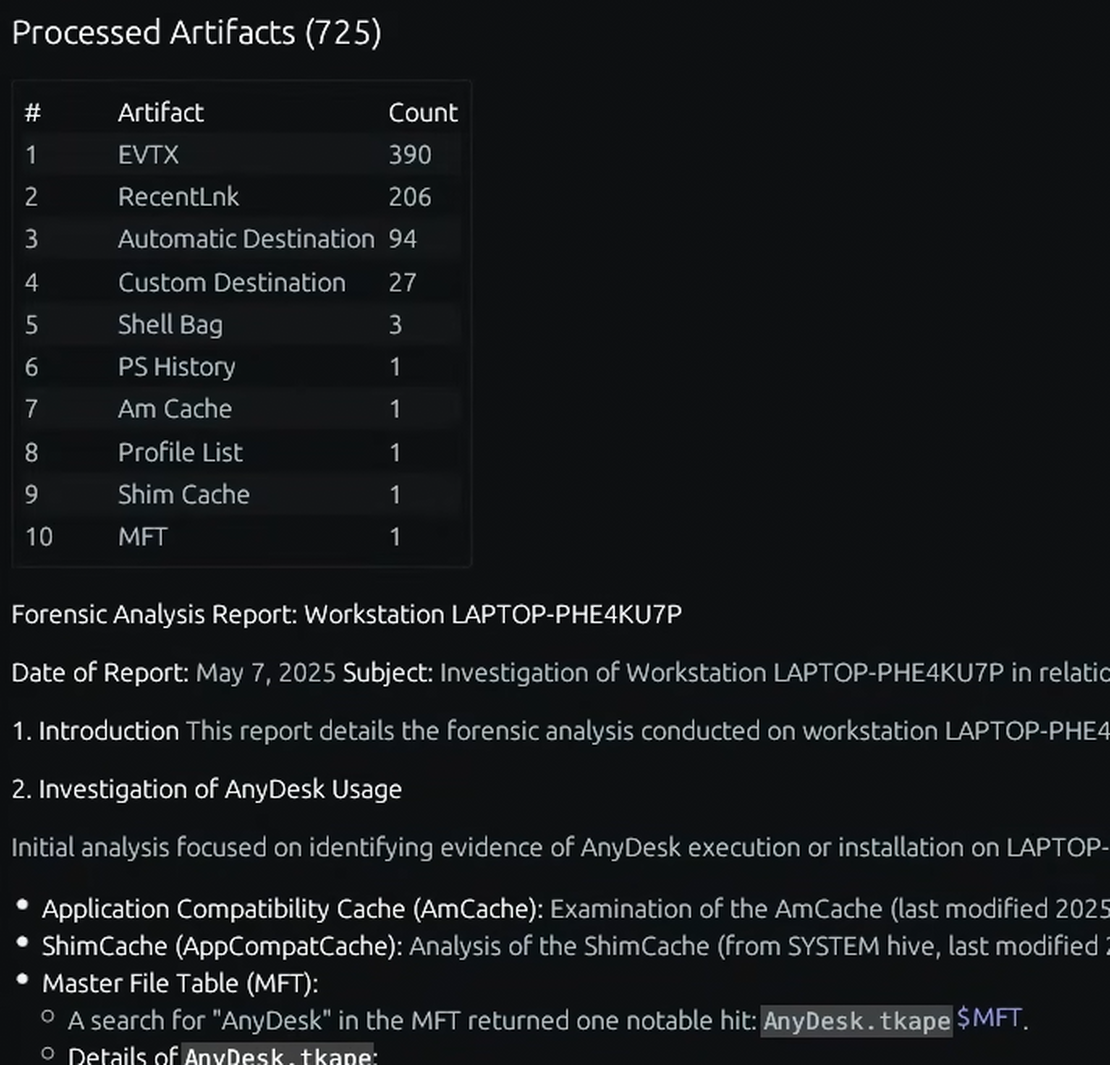
Unified reporting and intervention.
Access and manage findings through an intuitive web platform. Every AI-generated insight is directly linked to its underlying forensic proof, giving you absolute confidence to act.
- Web/Native
- Device Actions
- Case Workflows
- User Management
and, much more
A full spectrum of advanced forensic capabilities, making deep historical analysis and proactive threat hunting an accessible, continuous process for organizations of any scale.
Deep Historical Insight
Access years of forensic data, even predating TensorGuard's installation, to uncover long-dormant threats and reconstruct past device activities.
Intuitive Indicator Views
Empower your team with TensorGuard's 'Indicators' that translate complex forensic data into easily understandable events, no deep forensic expertise required.
Unlimited Endpoint Scaling
Establish a comprehensive forensic baseline across your entire device fleet, moving beyond the cost-prohibitive limitations of per-device consulting hours.
EDR Complementation
Enhance your existing EDR by filling the historical data gap, creating a complete security posture that fuses live prevention with strong forensic truth.
Proactive & Continuous Monitoring
Schedule intelligent reporting to automatically hunt for threats using digital forensics as a novel data source, continuously identifying risks before they become incidents.
Targeted Activity Search
Instantly query your entire fleet for specific activity. Answer critical questions like, "Has this malicious tool ever run on any of our servers?" in seconds with directly cited forensic evidence.
Connect with your forensic sources
Gain invaluable forensic insight empowering youto make data-driven decisions.
Explore All Artifacts
AmCache

Event Logs

Jumplists

MFT

Microsoft 365

Profile Lists

PS History

Recent Lnks

Shell Bags

ShimCache

Slack

SRUM

Web Browser

AmCache

Event Logs

Jumplists

MFT

Microsoft 365

Profile Lists

PS History

Recent Lnks

Shell Bags

ShimCache

Slack

SRUM

Web Browser
Start with a Compromise Assessment.
The best way to see the power of TensorGuard is to use it. For a simple, flat fee, we will conduct a full, AI-powered Compromise Assessment on a selection of your critical systems.